Find some of the most useful PowerShell commands and scripts for Windows Server 2016 and 2019
Sometimes using Windows PowerShell versus the GUI interface saves time and headaches. Below is a preferred list of PowerShell commands we use on Microsoft Windows Server 2019 and 2016 operating systems.
As a Managed IT Services Provider (MSP) we can save hours using PowerShell commands, especially when provisioning tens of servers for our data center or customer infrastructure. As we find more commands that are practical for the more common scenarios we will add them to the list below. Please note that many of our PowerShell commands listed below will also work for Windows 10 operating systems.
Obtain your Active Direcotry Globally Unique Identifier (GUID) for your Office 365 domain
Get-ADDomain
# Look for your ObjectGUID in the results. You can also run Get-ADDomain on a locally joined workstation.
Default Execution Policy - set to unrestricted
Set-ExecutionPolicy Unrestricted
Disable Windows Error Reporting
Disable-WindowsErrorReporting
Disable Automatic Windows Updates
Set-ItemProperty -Path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU -Name AUOptions -Value 1
Disable Windows Reboot Schedule (Active hours)
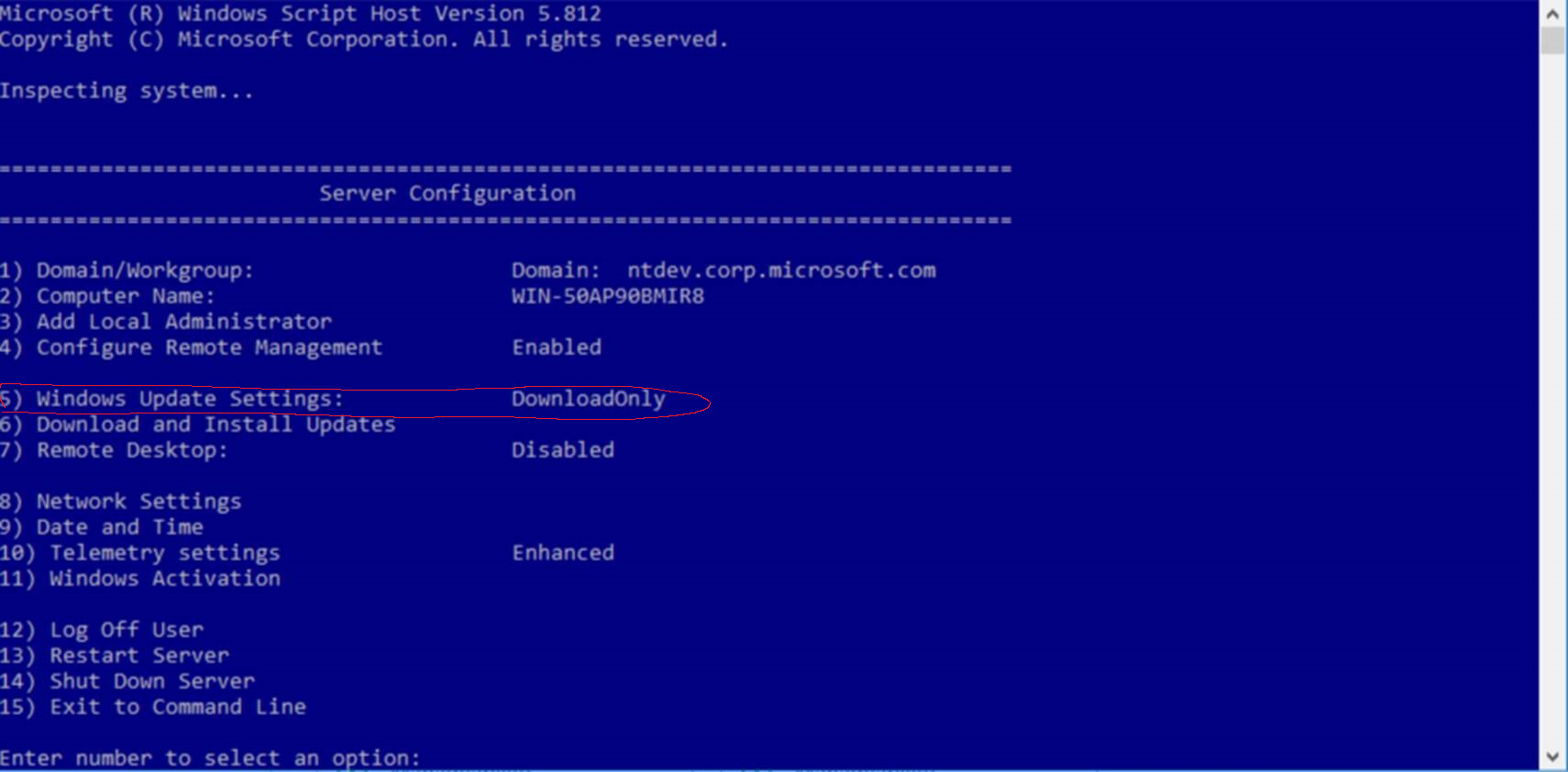
1) Open Windows Powershell by right click > run as administrator
2) Type: SCONFIG and hit enter
3) Press 5 (Windows Update Settings)
4) Press D (Download Only mode)
5) Close Powershell
Enabling Remote Desktop with PowerShell Remotely
Invoke-Command -ComputerName client01 {Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server'` -Name "fDenyTSConnections" -Value 0; `Enable-NetFirewallRule -DisplayGroup "Remote Desktop"}
Restart Windows Service with PowerShell
Restart-Service <service-name>
EXAMPLES
Restart the spooler (printing) service:
restart-service spooler -force
Find all the network services on the computer (starting with "net...") and restart any that are stopped:
get-service net* | where {$_.Status -eq "Stopped"} | restart-service
Enable and Disable Windows Defender Firewall with PowerShell
To enable Windows Defender Firewall for all network profiles:
Set-NetFirewallProfile -Enabled True
To disable it for all, use:
Set-NetFirewallProfile -Enabled False
Enable and Disable Windows Defender Antivirus with PowerShell
Enable Windows Defender Antivirus:
Set-MpPreference -DisableRealtimeMonitoring $false
Disable Windows Defender Antivirus:
Set-MpPreference -DisableRealtimeMonitoring $true
Uninstall Windows Defender Antivirus:
Uninstall-WindowsFeature -Name Windows-Defender
Disable Windows Display, Monitor Timeout to Never
powercfg -change -monitor-timeout-ac 0
PowerShell Command to Check TLS Version in Windows
Copy the code below and save it into a text file with the extension .PS1 (PowerShell script). Execute the script in an elevated PowerShell window.
---------
$ServerName = Read-Host -Prompt 'Input your server name'$Port = Read-Host -Prompt 'Input your server TCP port number (443 is most common)'nmap --script ssl-enum-ciphers -p $Port $ServerName
Script to disable old TLS versions
Copy the code below and save it into a text file with the extension .PS1 (PowerShell script). Execute the script in an elevated PowerShell window.
---------
function disable-ssl-2.0
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -Force
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -name 'Enabled' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'Enabled' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'DisabledByDefault' -value '1' –PropertyType 'DWORD'
Write-Host 'Disabling SSLv2'
}
function disable-ssl-3.0
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -Force
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'Enabled' -value '0' –PropertyType 'DWORD'
Write-Host 'Disabling SSLv3'
}
function disable-tls-1.0
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'Enabled' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'DisabledByDefault' -value '1' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'Enabled' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'DisabledByDefault' -value '1' –PropertyType 'DWORD'
Write-Host 'Disabling TLSv1.0'
}
function enable-tls-1.1
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'Enabled' -value '1' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'DisabledByDefault' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'Enabled' -value '1' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'DisabledByDefault' -value '0' –PropertyType 'DWORD'
Write-Host 'Enabling TLSv1.1'
}
function enable-tls-1.2
{
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value '0' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' –PropertyType 'DWORD'
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value '0' –PropertyType 'DWORD'
Write-Host 'Enabling TLSv1.2'
}
function enforce-tls-versions
{
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Services\RasMan\PPP\EAP\13' -Name 'TlsVersion' -value 'F00' –PropertyType 'DWORD'
}
disable-ssl-2.0
disable-ssl-3.0
disable-tls-1.0
enable-tls-1.1
enable-tls-1.2
enforce-tls-versions

