We cover how-to set up a pfSense, Sophos XG, and Cisco Firepower virtual firewalls on Windows Hypervisor with multiple vLANs
It's easy to forgot the various steps and requirements for setting up a virtual firewall, like the open-source pfSense, Sophos XG-v, and the Cisco Firepower FTDv on a Windows Server Hypervisor. We outline the requirements, initial configuration, and a few tips to ensure you do it right the first time.
THE VIRTUAL FIREWALL & HYPERVISOR REQUIREMENTS
You'll need two network cards and make sure that the ones you'll be using are certified compatible with the Hypervisor engine. This is equally and maybe even more important in the VMWare ESXi world, but is still a good idea. Next, you'll need to ensure that you have, at least, Windows 2012 R2 or higher. We've had some troubles getting the new-age NGFWv to work on older version of Windows, and at this point, you shouldn't run anything end-of-life anyway. With that out of the way, you're ready to create your two virtual switches.
- Two compatible network interfaces- a dual link Ethernet card or mixed hardware is fine.
- Windows 2012 R2 or higher operating system- fully patched and updated with the latest feature release with the Hypervisor role installed.
- Two Windows Hypervisor virtual switches.
The Virtual Switches
Inside the Hypervisor Manager, open the Virtual Switch Manager and create your first virtual switch (VS). We're going to start with the WAN facing interface; make note of the physical network card that you plan on having the WAN or Internet circuit plugged into.
This virtual switch should be configured with the type as EXTERNAL. Make sure that you've selected the right network interface card that will pass traffic to the Internet.
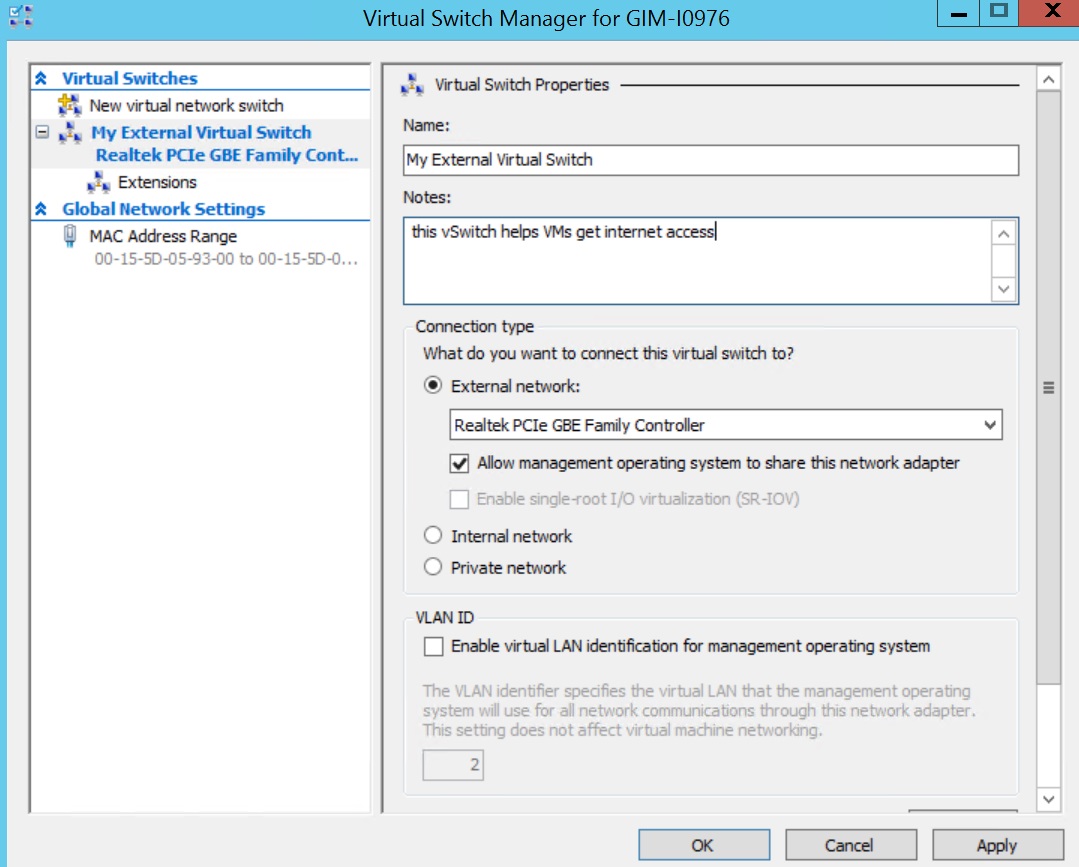
Next you need to create the local area network LAN virtual switch.
We have always gone with the same settings (EXTERNAL connection type) but choosing Internal or External can provide the same results. One the extra step you may need to take is allowing the LAN virtual switch to accept and pass traffic from multiple VLANS.
If the virtual firewall configuration or design that you are installing DOES NOT have multiple VLAN interfaces you can skip the next step. If you do have multiple LAN interfaces (vLANS) then you'll need to run a PowerShell script. But first it's time to install your virtual firewall.
We're not going to walk you through the installation steps to install the virtual firewalls- you can Google "Install <firewall brand> on Hypervisor" for the unique step-by-step instructions. Once you have the virtual appliance installed consider the following section.
IF YOU PLAN TO HAVE MULTIPLE VLANS ON YOUR HYPERVISOR VIRTUAL FIREWALL RUN THIS POWERSHELL COMMAND
Open a CMD prompt in elevated mode.
Run the following command- adjust the VMName to match the name of your virtual firewall, and specify what VLAN IDs you want to allow through the firewall.
PS C:\> Set-VMNetworkAdapterVlan -VMName <nameofyourvm> -Trunk -AllowedVlanIdList 1-100
If you skip this step and have multiple VLANs, your firewall won't be able to accept the tagged packets that originate from your managed switches.
