What is Microsoft Office 365 Advanced Threat Protection?
Office 365 Advanced Threat Protection (ATP) safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools. ATP includes:
- Threat protection policies: Define threat-protection policies to set the appropriate level of protection for your organization.
- Reports: View real-time reports to monitor ATP performance in your organization.
- Threat investigation and response capabilities: Use leading-edge tools to investigate, understand, simulate, and prevent threats.
- Automated investigation and response capabilities: Save time and effort investigating and mitigating threats.
Office 365 ATP Plan 1 and Plan 2
ATP is included in Office 365 E5; however, ATP Plan 1 and ATP Plan 2 are each available as an add-on for specific subscriptions. To learn more, see Feature availability across ATP plans.
Three advantages
To leverage Microsoft's Advanced Threat Protection, it’s essential to know about the strengths of its threat intelligence, especially in the antiphishing space.
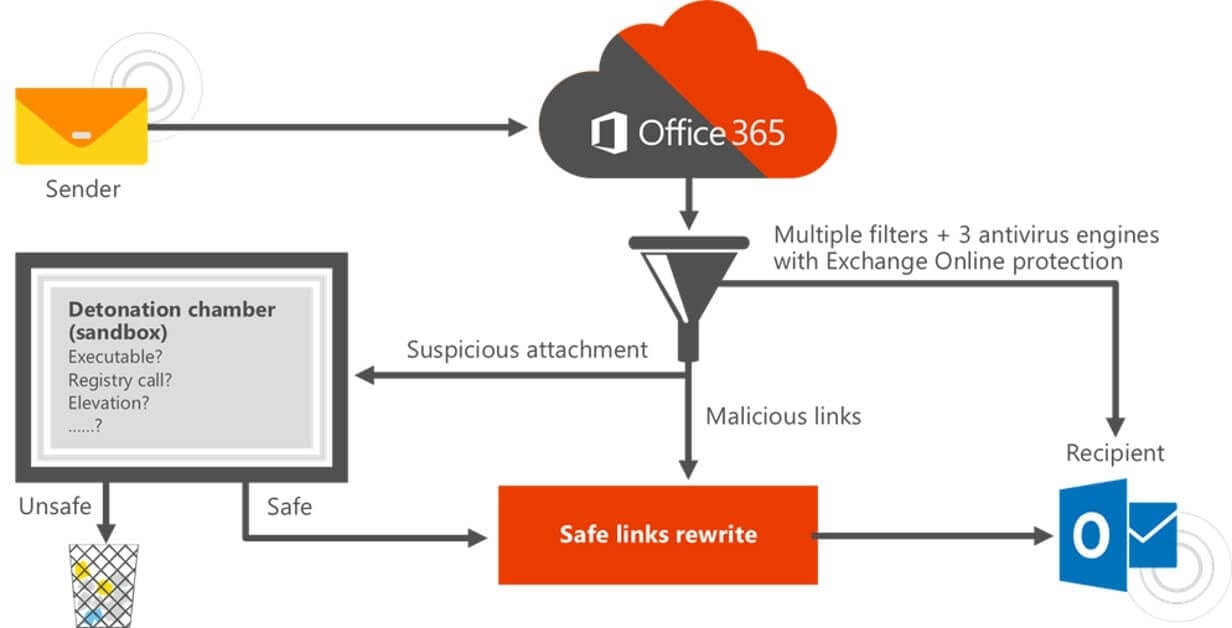
- URL rewriting. A feature available in Advanced Threat Protection for Office 365, Safe Links provides time-of-click verification of URLs in emails and Office documents. When activated, it rewrites every domain to route users through ATP Safe Links protection before redirecting the end user's browser to the webpage. It checks if that destination domain is not on a custom blacklist of malicious URLs created by the organization, or on the Microsoft blacklist.
- Attachment sandboxing. Advanced Threat Protection calls this feature Safe Attachments, which detonates malware in a secure environment to learn its behavior. (Google’s G Suite doesn’t have attachment sandboxing yet, but it is in beta at the time of this writing.) Millions of Office 365 users whose files have been sandboxed benefit from the scale at which the catch rate is honed. Better yet, this feature deploys in one click.
- Easy integration. Advanced Threat Protection integrates into Office 365 without requiring additional configurations or adding a mail flow connectors — the complicated path email secured by conventional solutions takes when it travels from one server to another and then back. It’s a simple checkbox to turn on, requiring no mail flow rules or connectors required. With conventional email security solutions, such as a Secure Email Gateway or Mail Transfer Agent, this is not the case and can become a time-consuming prospect during deployment and tune-ups.
Three Drawbacks
The popularity and wide-spread use of Microsoft Office 365 are its weakness.
- Predictable circumvention. For about $35 per month, any hacker in the world can create an Office 365 account to figure out how to circumvent the security. When analyzing new pieces of malware, Avanan security analysts see the creativity and complexity of code put in by the hackers to specifically evade Microsoft’s default security.
- Advanced Threat Protection is Version 1. Introduced in 2015, its features and functionality are relatively immature when compared to solutions established security companies have been honing for decades. The intellectual property incorporated into technology companies focusing purely on sandboxing — like FireEye, PaloAlto, or CheckPoint — are years ahead in their ability to consistently catch evasive malware.
- Opaque reporting and forensics functionality. Visibility and control in the Microsoft security interface are limited. This makes it challenging to deep-dive into a specific incident, find the root cause, which users are impacted, if a user account was compromised, if data was lost, etc. At the same time, ATP limits reporting based on time constraints. For example, it takes a few hours to return a mail protection detail reports for messages older than seven days. For data older than 90 days, reports are inaccessible.
Conclusion
Why does Microsoft fall victim to phishing attacks that get past Advanced Threat Protection and Exchange Online Protection (EOP) for Office 365?The reasons have nothing to do with any particular Microsoft failure, but much to do with the widespread use of Office 365. Because Office 365 is the most used platform, it is also the most attacked. This creates strengths and weaknesses in Advanced Threat Protection .Organizations should use Microsoft as a primary security provider and layer additional security solutions from third-parties that have more tailored AI, security that is invisible to hackers, and comprehensive reporting. Knowing this, Advanced Threat Protection empowers Office 365 admins to use the platform responsibly and optimally.
