Phishing and Spoofing email attacks have risen by more than 200 percent since 2010.
Learn how to spot phishing and spoofing attacks in three easy to follow tips. While there are several ways to help mitigate these types of emails from making their way into your inbox, there's never a 100% guarantee.
Tip 1: Don't trust the display name
It's easy for someone to enter a fake display name, what's in the FROM: field.
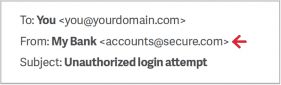
Check the email address in the header from--if it looks suspicious, don't open the email and simply delete it.
Tip 2: Inspect any links but don't click
If you hover your mouse over an embedded link (this applies to not only emails but websites too), you can see the exact place the link will take you. For instance, I can create a link www.chase.com, but if you hover your mouse over the link, you can see that the actual address is https://itecsonline.com.Web browsers usually have the preview of the actual address the supposed link will take you to in the bottom right-hand corner. Outlook displays the link information directly above your mouse icon.
Tip 3: Don't click on attachments
Malicious attachments can have embedded viruses, if you weren't expecting the email or attachment, don't open it.
